It struck me how obvious this was when I heard a customer mention the name of the virus: “Smart Fortress 2012”. I thought, this is another one of those fake malware applications that I’ve seen time and time again. Since this user’s computer was infected while running an up-to-date version of a virus scanner, it proves the general ineffectiveness of most of these applications. I thought that it would be a good idea to explain how I go about removing these things – but with the fact that they’re all the same, you can’t follow instructions exactly. No two of these things are created equal. My hope is that, if you get a virus that acts like this, you can use some of these tactics to get rid of the program yourself.
Step #1 – Identify the filename and location of the malware
This is often the most difficult stage since you must find a way to open a task manager, but the malware will block applications such as Task Manager, AutoRuns, and Procexp. You’ll want to try running any of those and if you still can’t get them loaded, try using my tool Prockill. Using any of these tools will hopefully get you to the point where you can see something like this:
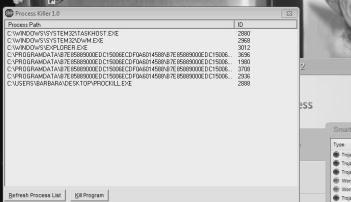
Now, the screenshot is small and grainy (I had to zoom way in on that picture) – but it represents a view of the screen for the few seconds before the malware was able to close Prockill.
Sometimes you’ll need to actually use Windows Explorer to go to that folder and copy the actual filename (if it’s something long and random like this one).
Step #2 – Kill the process
This step is often harder than it seems because some malware opens as multiple processes and or in multiple locations. Even worse, many of load multiple processes and back each other up. What you’re after is making some progress – so go after the main process loaded (so far as you can see). In this case, you still may not be able to use Task Manager or other process killer, so again Prockill can help. What I do is make a shortcut to the Prockill file I’ve downloaded and change the shortcut’s properties to this:
The string you see in the above target tells Prockill to close anything with the name of the offending process we found in step one. The full test of the target in my case was this:
C:\Users\testuser\Desktop\ProcKill.exe /n:B7E85889000EDC15006ECDF0A6014588
Step #3 – Take basic corrective action
This situation had Smart Fortress 2012 loading by way of a modification to the registry’s .exe associations. Once I was able to kill the main process, I then found one of the widely available registry fixes on the Internet and created a simple .reg file and imported those details to reset the association. This then allowed me run other applications.
I went to the folder where the malware was located and fully deleted those files, and then checked autoruns to see if I was missing anything else (and deleted those files if anything else was found).
After this, reboot the system.
Step #4 – Finish with full corrective action
After the reboot, ensure that what you did enacted changes you expected. If the virus returns as it was, you’ll have to take a more serious approach. If the progress is clear, then it’s time to clean up and remove anything else that was left behind.
– Make sure your virus scanner is working properly (re-install and update if you have to)
– Do a full scan of the computer (consider using an offline scanner)
– Remove any links or files left behind to the malware
– Consider clearing out the System Restore data and then re-enable System Restore
– Run all Windows and other product Updates
If you’d like more help on these types of scareware of viruses, be wary of sites that offer free scanners or other tools to remove the infection. Be sure to take all of the advice you get with a very critical eye. These types of applications aren’t going anywhere, so be safe. Most importantly: DON’T EVER RELY ON ONLY A VIRUS SCANNER TO PROTECT YOU.