How does this work? Let’s say you’re Twitter password is the horrible “123456”. With this passphrase go to a hashing site and enter in the service name (this will be case sensitive) and your passphrase. It looks like this:
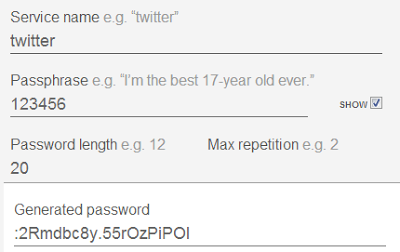
With that, you copy the text “:2Rmdbc8y.55rOzPiPOI” and set it as your Twitter password. Every time you need to login to Twitter, open the hashing site, enter the same details as above and the generated password will be the same thing. Just copy the generated password text into Twitter and log in.
Some of the trouble with using these tools revolves around you particular trust level. Of course, these are web sites and because of that, it’s possible for any of them to capture this information. If this process were offline completely, it may be more appealing. In the same way, because these are sites that require an Internet connection, you may find yourself lacking access to them (especially if the password you’re after is the one that can only be looked up offline).
Certainly, the power of this process is that your password is changing based on the site name and the Passphrase you use. Using a nice long passphrase like “The long dog walks under salty trees” would make the generated password much stronger. All of these sites say: “This site does not store or transmit any data you enter into it; the information you type in never leaves your computer.” which is the ideal situation – though unverified. It also appears as though the software behind the hashing is open source.
Some password hashing sites to check out are: SuperGenPass, getvau.lt, Mawud. Take a look and let us know what you think. Would you use something like this?