Download here (ZIP)
Over the years, this tool has proven popular. CRCutil was one of the original utilities offered on a previous incarnation of this blog. As always, most programs on this blog are free to download and include all source code required for the program. The idea from CRCutil’s inception was to allow you to use and create applications that can encrypt and decrypt text or compare files. Due to drastic changes in dependencies (which I’ll describe later), CRCutil isn’t as useful as it once was.
The CRCutil application in its current form retains two core uses:
1. Comparing two files
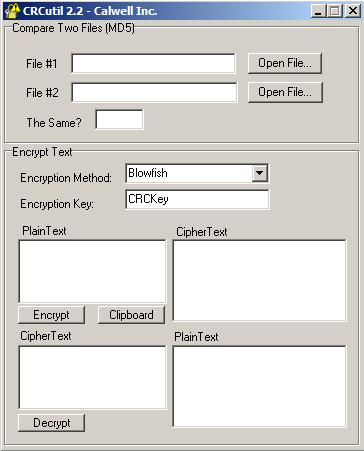
You may want to use this to test if two files that are supposed to be the same, are in fact corrupted in some way. The MD5 test is one of the more reliable means of testing files for corruption. In many applications, a CRC value is created from a file, provided with an archive, and then tested against that archive later on to ensure integrity. Many software packages make use of this technology to give the user the option to test for corrupted files.
2. Text encryption
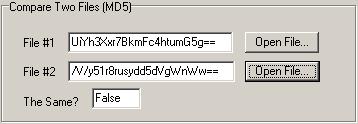
This method of encryption is becoming more popular so it would be an interesting thing to create a utility that could encrypt and decrypt small amounts of text (say an entire e-mail). With this, you could give this utility to your friend, agree on a key string, and only send an encrypted text to them, they would take that text, copy and paste it into CRCutil and convert the encrypted text back to readable form. Here is an example:
I decide to send my friend a message I encrypted with CRCutil, the result of the encryption using Blowfish as the Encryption Method and “CRCKey” as the Encryption Key would be:
dlrujwould8GJbrSVwFU51VQZx4dYpkNQiP5EoAAVxEmmix71hMu
My friend then runs CRCutil, copies that text into the “CipherText” field of CRCutil and when my friend clicks Decrypt, the following message is displayed under “PlainText”:
Hello,
I just wanted to say hi!
Kevin
The Source Code
Built exclusively on Delphi 5 some time ago, CRCutil uses Delphi Encryption Compendium (DEC) 3.0 components to encrypt and decrypt data. The difficulty with this is that Delphi 5 is hard to find (if not impossible) and the functions inside of newer versions of DEC require CRCutil to be rebuilt to a certain degree. You should expect difficulties getting the DEC 3.0 components working with Delphi 6 and higher due to a number of changes. So, the utility is one of it’s time. Not necessarily a waste, but not as useful source-wise today. There are a number of better ways to do this today, and that may be something to try again in the future. The key file in the source is unit1.pas. This is where we call the required events to encrypt and decrypt text and run CRCs on files.
The first operation is the CRC on a file. You will want to have access to a file name (including path) to send to the hashmanager1.HashClass.CalcFile() function. This function will return a CRC value that may resemble “S/sd8g==“. I run this operation on a file twice and then compare the values in Edit1.Text with Edit2.Text. This then is used to place the text “True” or “False” in Edit3.Text. If you were to enhance this, you may want to add a reference to the file in the main dialog, or add a listbox or Explorer interface that allows for multiple files.
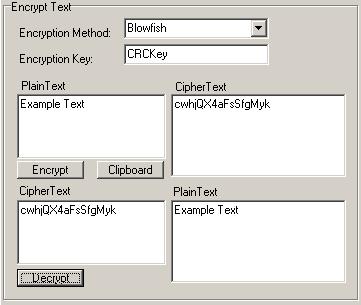
The second section of CRCutil is text encryption and decryption. Given that DEC supported a bunch of different types of encryption, so it made sense to expose all of the following:
BlowFish, 3Way, Gost, IDEA, Q128, SAFER-K40, SAFER-SK40, SAFER-K64, SAFER-SK64, SAFER-K128, SAFER-SK128, SCOP, Shark, Square, TEA, TEA extended, Twofish, Cast 128, Cast 256, DES Single 8byte, DES Double 8byte, DES Double 16byte, DES Triple 8byte, DES Triple, 16byte, DES Triple 24byte, DESX, Diamond II, Diamond II Lite, FROG, Mars, Misty 1, NewDES, RC2, RC4, RC5, RC6, Rijndael, Sapphire II, Skipjack
The user can encrypt text and view and decrypt the output (using the text they may have encrypted previously). Once a string is encrypted, the user can use the “Clipboard” button to copy the encrypted text to the clipboard. By default, the property EncryptionType as BlowFish and then executes the following as the user clicks on a button:
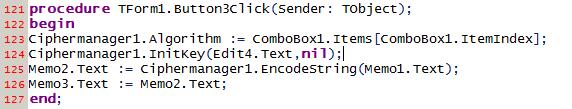
Text encryption relies on an arbitrary key value that is designated for the encryption engine. This unique key is what is used to encrypt the text. This initializes the encryption engine using the hard-coded key and then uses the EncodeString() function to place text in Memo2.Text.
So, hopefully, you enjoyed playing with encryption and this application may come to some use. This technology is one of the first attempts at using encryption to make a tool. As you’ll see, these ideas evolved into other tools. If you have any thoughts or ideas about this tool, please do let us know. The crcutil.exe file was scanned by VirusTotal current as of August 29th, 2012. if you would like to see that scan report, please click here.