Recently, I was asked a question “How can I tell if someone has placed spyware in my computer to track my stuff or remote control to see what I’m doing?”. It’s natural to fear the worst when complicated systems might have been left in the hands of those who might be somewhat untrustworthy. In this article, I’ll try to go over some of the ways you can tell if these things might be happening, and how to prevent some of them from occurring altogether.
So, it should come as no surprise that I’m quite interested in what can be done to combat threats on a Windows computer with tools you already have. Today I’m going to look at three tools you’ll find on most any Windows flavour out there: Windows XP, Windows Vista, and Windows 7. Namely, wmic and taskkill. This is going to be more of a beginning overview of how you might use these tools to identify and stop a rogue application on your computer
When you’re in this business of fixing and maintaining technology – one of the most common questions you’ll be asked is “What do I look for in a new computer?”. While I’m usually obliged to ask for more about the prospective computer in question – sometimes the brand names come up and sometimes it’s just a general question because the customer wants to buy a new one. Coming to me (the IT Guy) is a good step and a worthwhile use of time, but without me, what kind of stuff can you do to find the computer that’s best for you?
You want to explain what’s happening, but you’re no technology expert, right? Well, I want to let you in on a very important little secret. How you describe your issue and the questions you ask are essential to correcting your issues. Here, let me show you how to master this very important skill.
Apparently, the most common way to destroy a phone is by dropping it into a toilet (though, you want to take “studies” with a grain of salt). If you’re a heavy mobile phone user, at some point you’ll drop your phone or device into some liquid substance at some point. I had the same thing happen to my laptop, and I wanted to share how I managed to return the laptop to a working state.
I take lots and lots of screenshots on all the platforms I use. One of the best platforms for screenshots, however, is the Mac. You may know that on the OS X platform, a region-based screenshot is extremely easy to do with a Command-Shift-4 keyboard shortcut. Nothing like that exists on Windows (except for the print […]
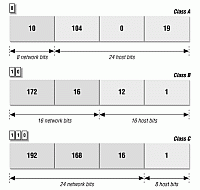
While these practices all work, this industry is begging for consistency and there are recommendations as to the proper use of IP addressing to simplify your network management. Have you ever wondered why a network’s hosts might be numbered 10.x.x.x or 192.168.0.x?
- 1
- 2