Malware: A Fast Way To Clean Up The Group Policy Mess After A Virus
So, you’ve cleaned an infected Windows PC and yet some stuff still lingers. You can’t right click on the desktop, you can’t get into task manager and you just know that a host of other policy related stuff is going on. Often, with Virus Scanners, they’re adept at removing files and folders, but they’ll leave behind things like registry settings (often taking the form of Group Policy changes). These settings can be just as harmful as the initial infection itself.
I’ll show you the fastest way to get past all of that and get your Windows PC to a point where you might be able to use it or do a deeper virus scan . Please do note, this article references editing the Windows Registry. This is dangerous and can cause some serious trouble if you aren’t careful. Do not undertake registry changes lightly. Always backup your registry before starting.
I should note that in a corporate Active Directory scenario, these points and issues are less likely to apply. The Group Policy settings enforced by the domain may supersede some of this, so tread lightly (or contact an Administrator, if you have one).
First you need to get into the registry
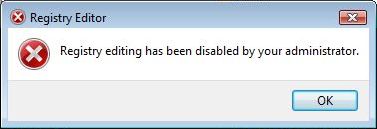 |
| What happens when regedit is disabled |
There are a couple ways to go about this. First, while in windows, try and run these two commands:
First Command:
REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableRegistryTools /t REG_DWORD /d 0 /f
Second Command:
REG add HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableRegistryTools /t REG_DWORD /d 0 /f
If that doesn’t work…
This should let you run regedit right away. If not, reboot the system, press F8 at boot and load “Safe Mode with Command Prompt” and run these two commands:
First Command:
reg delete HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v “DisableRegistryTools”
Second Command:
reg delete HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System /v “DisableRegistryTools”
Reboot, then, open regedit. If you still can’t get in, you may not have cleaned the original virus. You’ll want to go back and continue to work on cleaning that. Once in the Registry Editor, we can now do a quick cleaning of policy settings.
Clean it Up
First, Look for this key in the registry:
[HKEY_CURRENT_USER[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies]
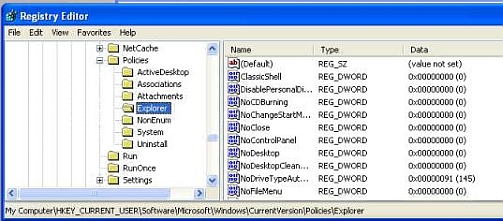
Once you get there, just delete every single sub-key on the list. In the pictures below, I would delete “ActiveDesktop”, “Associations”, etc. In a clean system, none of these keys is necessary, so it’s okay to delete them all.
An Infected Machine will look allot like this:
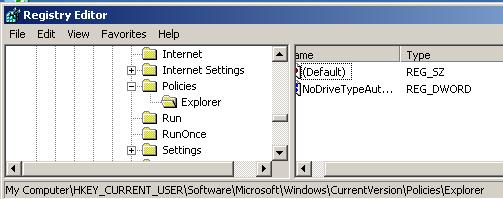
A clean machine looks more like this:
Then, look for
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies]
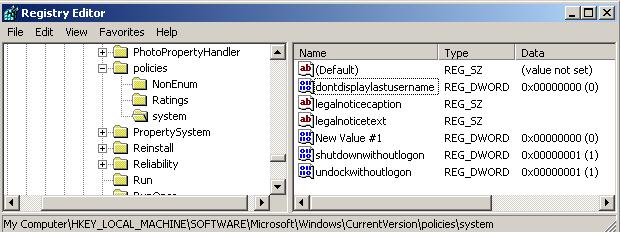
You will want to keep some of this, so I would suggest simply removing anything not showing in the following graphic (of a clean system). Leave the NonEnum and Ratings alone and focus on what might be sitting in the system folder.
Restore the Start Menu to defaults
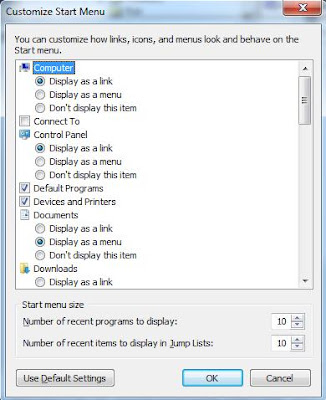
In Windows 7 (and later), you can rest the menu to defaults by right-clicking on your Taskbar and choosing “Properties”. Find the Start Menu tab and click “Customize” The “Use Default Settings” will reset the Start Menu.
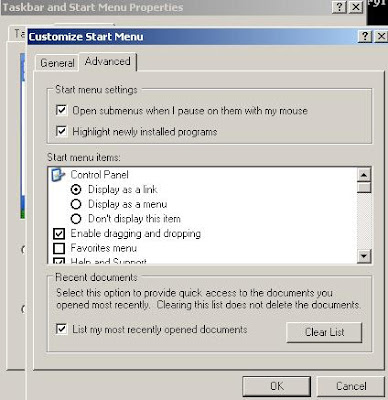
In Windows XP, you’ll have to manually enable parts of the Start Menu by right-clicking on your Taskbar and choosing “Properties”. Find the Start Menu tab and click “Customize” and look for the “Advanced” tab. In here, individually turn on parts of the Start Menu to get them back.
Reboot
Yes, reboot the machine and you should have the offending policy settings taken away as well as the Start Menu restored. Now you can run a deeper scan of your system and attempt to remove anything else that may be of issue. Do you have any other suggestions for cleaning a machine?