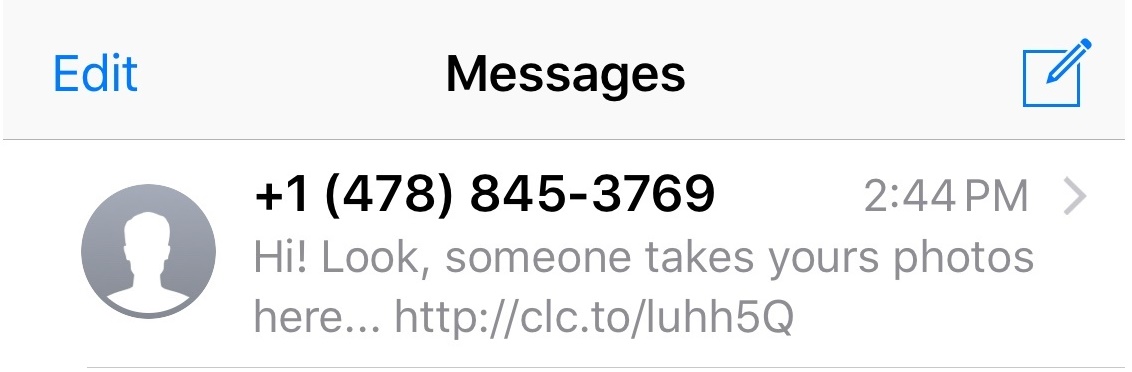
Phishing is the most common way bad guys steal your passwords and hook viruses into your machine. This is routinely done via email, but this practice is becoming more popular in SMS messages in a practice Forbes has called Smishing. Today, I received one such message and thought I’d go deeper and get to the heart of this malicious phenomenon.
Just like medical journals, it seems like every new day brings some new report or another on the “state” of technology. Some reports are “nothing is secure, and you can never be secure”, while others take a more restrained “Apple owns everything” approach. I’m always sceptical when I hear of these things…
The most important line users cross with any software is the point of running (or installation). This is usually where you have a need to fulfill (like play video), and a software title in mind (like VLC Media Player). But, since you’re a cautious user who doesn’t assume a virus scanner is perfect, and you don’t […]
Email phishing scams are all too common. Let me take you inside one such scam and show you how it works, and how to avoid similar tricks.
Bad design can creep into any process, whether small or the much larger Twitter. I was thrust upon this when I (rather innocently) changed my phone number – but forgot to turn off Twitter’s “login verification” process first. There is no way I could have known, but my specific use case of Twitter, coupled with a phone number change, locked me out. After much consternation, I understood Twitter’s two-step process is broken.
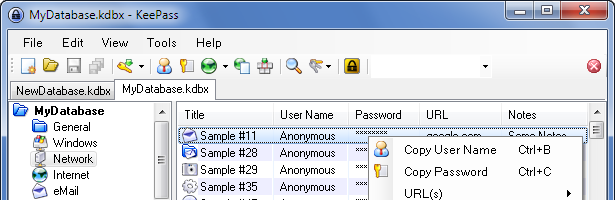
I generally gush about how amazing this tool is – I’m perplexed as to why there isn’t a great version of this tool on OS X. It doesn’t make sense that an operating system so powerful is so woefully underserved in this regard. As a daily OS X user, you too may wonder what the hell is up with KeePass on OS X, so let’s take a look.
The anti-virus (AV) application is dead, right? This often bloated, resource-intensive application has to scan every single file on a computer; but still misses that one malicious application that brings your network to its knees.
Bluepass, a new tool (like Keepass) that intends to have cross-platform support and a new syncing feature for your data. Bluepass is currently in its early stages and looking for support.
This is what seems like a tipping point, as many have started to seriously question the effectiveness of locally installed Virus Scanning applications. This idea of depending on virus scanning applications has been on my mind, and I wanted to flesh it out.
- 1
- 2