You might have heard talk of a new way to secure systems and that it involves something described as Two Factor or 2FA. What you need to know is that it’s an extra layer of protection on your accounts that can protect you from hackers. The idea is that while a hacker may have gotten […]
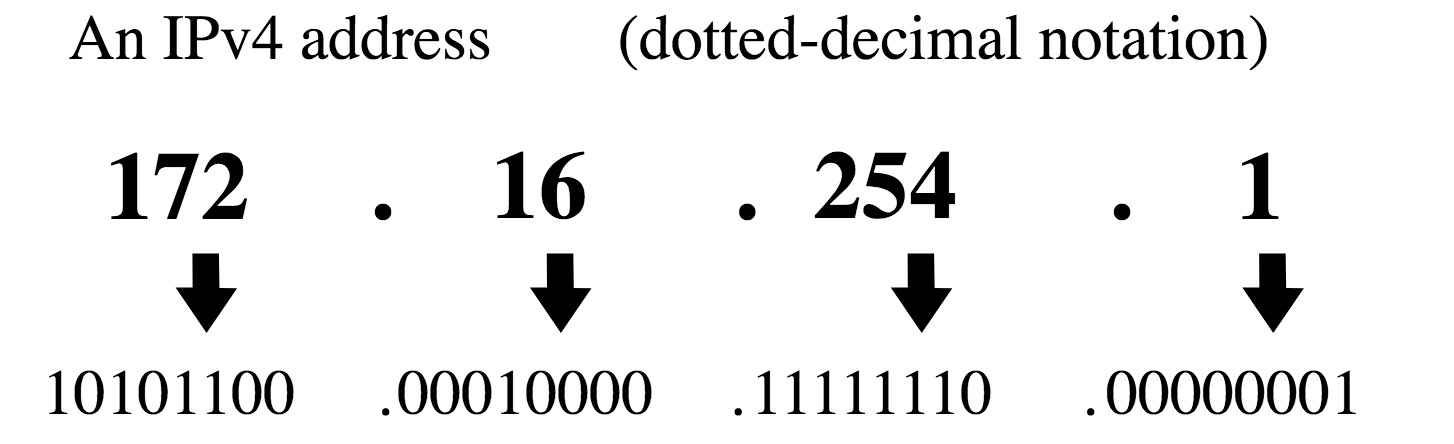
Internet Protocol (IP) is the general basis for all communications on local and Internet networks. These communications rely on some basic numbers that identify you to other computers on the local network, and to the world. Those numbers put together are what’s commonly called an IP Address. On occasion, someone in you IT department or support might ask you to provide this number format, and I’ll show you how to find it.
While in the Dominican Republic I made it my personal mission to gain data access on my smartphone. Over the years, this process has become easier as the companies have accommodated smartphone users. With an unlocked smartphone, you can get reliable and useful pre-paid cell phone and data access in the Dominican. I’ve learned a few things along the way that you’ll want to know if you plan to do this.
For many, learning to create an application seems out of reach. When I’m trying to understand something, it can be good just to start and explore. This guide will show you the basics of building a Windows program; from downloading the free development tools to coding a basic application, to testing it. There are many tools, languages, and environments from which to develop, but if you just wanted to get started with something simple – this is a good place to start.
The most important line users cross with any software is the point of running (or installation). This is usually where you have a need to fulfill (like play video), and a software title in mind (like VLC Media Player). But, since you’re a cautious user who doesn’t assume a virus scanner is perfect, and you don’t […]
Taking screenshots is one of the most common things you’ll do with your computer. You may want to record something you can’t easily save, and want it clearer than taking a picture of your monitor would yield. Today’s Basics article is about taking screenshots.
The scenario: You need to get a copy of Microsoft Office 2010 installed on your Windows-based computer, but don’t wish to buy a copy the Application. You heard there were free options available for this software but we’re sure how to get the application installed. Included in Microsoft Office 2010 Starter are stripped down versions […]
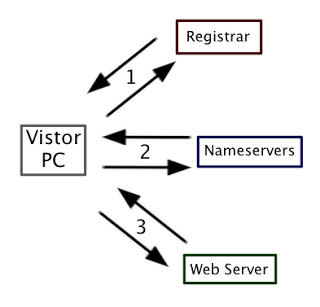
So, you have a website or domain and are hosting useful services like email, a website and possibly even cloud storage. This is all great, but the day comes when you want to make changes or an expiry happens and the “Hosting” word rears it’s ugly head. Who is hosting my servers? What do I need to have a website or keep it online? What are all the key elements of a domain or website? Look no further, I will explain this (and more).
When asking a Tech Support person, or someone you trust to remotely assist you, they may ask you “What is your computer name?” or “Please find me your computer name”. This process can be quite challenging for some people since every new operating system seems to change the process ever so slightly (while manufacturers, don’t).. Well, fear not – I’m going to list the simplest of ways to get that information so you can supply the details you need and move on.
Recently, I was asked a question “How can I tell if someone has placed spyware in my computer to track my stuff or remote control to see what I’m doing?”. It’s natural to fear the worst when complicated systems might have been left in the hands of those who might be somewhat untrustworthy. In this article, I’ll try to go over some of the ways you can tell if these things might be happening, and how to prevent some of them from occurring altogether.
- 1
- 2