For those that run the free version of RustDesk’s open source remote access server one big missing good address book. The RustDesk client is good for one-off connections, but a paid license is needed to get the full-featured web address book. This may change in 2026, but for now, many are looking for a decent […]
As this fellow was booting up the computer, an unusual thing started to happen: the keyboard wasn’t working or initializing on boot. Not only that, but also the built-in mouse was failing. Now, if one were to connect the power, or perhaps an external USB-based mouse, the computer’s keyboard would then work. Disconnect all this, shut down the computer completely and no keyboard….
As you probably know, ISBN, the International Standard Book Number is one essential part of getting your book published. This unique number identifies each version (and edition) of your book to publishers and booksellers alike. I’m going to show you how to get one for free…
News that Amazon is changing the way they offer their e-books books in Digital Rights Management (DRM) free formats. DRM is that evil force of enshittification that locks your media to a device or ecosystem as a means of protecting authors and destroying interoperability. Naturally, authors are keen on protecting their works from rampant copying, […]
The problem I set to tackle today related to the glut of cwl.cc page references found on search engines that were of no value outside. How was I going to remove these in the most elegant way possible? In 2015, I actually covered this solution, but ten years later, I came at it again with a new theme and fresh eyes.
Thanks to Microsoft’s relentless drive to enshittify Windows we’ve all been playing ‘cat and mouse’ with their need to force logins to Microsoft accounts when Windows first boots. Microsoft’s push to force online logins is stupid and frustrating; and it won’t stop. Here’s a fix that I modified to improve so you have more options.
The directive was simple: Build some sort of tool that could perform an installation similar to what ‘sudo’ does on Linux in a limited user session. There is literally nothing like this for Windows that performs in any sort of automated fashion…
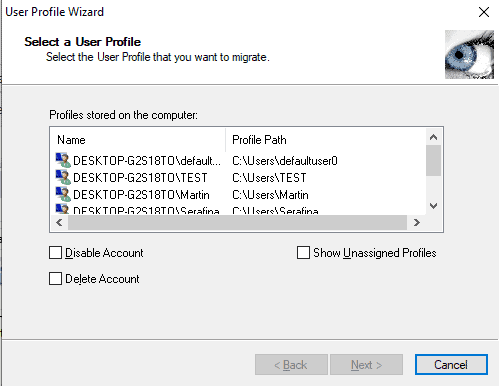
Moving user profiles from domain to domain has often been the topic of conversation. I’ve even written an article that took me more than a year to compile about the very act of copying or moving profiles. Now, we have Active Directory…
You want to install Zima OS, but want to try it in a virtual machine first. More specifically, in a Vmware Workstation virtual machine. I looked for more out there, and couldn’t find much in a Google search – I think some of that has to do with prior versions of ZimaOS (at least 1.0) […]
You might have heard talk of a new way to secure systems and that it involves something described as Two Factor or 2FA. What you need to know is that it’s an extra layer of protection on your accounts that can protect you from hackers. The idea is that while a hacker may have gotten […]